RSA
Main Source:
- RSA (cryptosystem) — Wikipedia
- Carmichael function — Wikipedia
- What’s the difference between RSA and Diffie-Hellman? [duplicate] — cryptography stackexchange
Rivest–Shamir–Adleman (RSA) is a widely used asymmetric encryption algorithm. It was based on similar mathematical properties with the Diffie-Hellman key exchange, that is large prime numbers and modular arithmetic.
RSA uses public and private key, the public key, which is shared publicly is used to encrypt, and the private key, which is kept secret, is used to decrypt. The key are related mathematically, however, it is computationally infeasible to derive the private key from the public key.
Explanation
Section titled “Explanation”The RSA is an actual asymmetric encryption algorithm (e.g., used for exchanging data), it is not used solely for exchanging key like the Diffie-Hellman key exchange.
It consists of four steps:
-
Key Generation:
-
Randomly select two large prime numbers which has large different, and . These prime numbers should be kept secret.
-
Compute , where is the modulus used for both the public and private keys. is also publicly available as part of the public key.
-
Calculate , where is Carmichael’s totient function, and it is the smallest positive integer such that , where is a positive integer, for all integers coprime to .
Since , , and since and are prime, , and likewise . Hence, , where is the Euler’s totient function.
The LCM itself can be calculated using Euclidean algorithm through the LCM formula, also is kept secret.
-
Choose a public exponent, , such that and ; that is, is coprime to . is also publicly available as part of the public key.
-
Compute as to obtain . is modular multiplicative inverse of modulo . can be obtained by solving using the extended Euclidean algorithm, using the properties of Bézout’s identity. This is kept secret as the private key exponent.
In conclusion, modulus and exponent is the public key. While exponent is obtained from , , and , these must be kept secret.
-
-
Key Distribution:
- The public key is shared with anyone who wants to send an encrypted message to the owner of the private key.
- The private key must be kept secret by the owner and should not be shared.
Sender must know recipient’s public key to encrypt message, and the recipient must use its own private key to decrypt the message. Similar when the scenario is reversed, if the recipient want to send message to the sender instead, then the recipient needs sender’s public key and sender will use their private key to decrypt the message.
-
Encryption:
- The sender must convert the plaintext message into a numerical representation, the plaintext will also be added with random padding, becoming .
- The sender retrieves the recipient’s public key and the modulus .
- The ciphertext is computed as .
-
Decryption:
- The recipient uses their private key to decrypt the encrypted message.
- The numerical representation of plaintext is calculated by .
- The original message is recovered by reversing the random padding scheme in the beginning of encryption scheme.

Source: https://www.practicalnetworking.net/series/cryptography/using-asymmetric-keys/
Security
Section titled “Security”RSA is used to encrypt message that is transmitted over insecure network. Attacker would intercept that encrypted message and decrypt it. In order to decrypt it, the attacker would need the recipient’s private key.
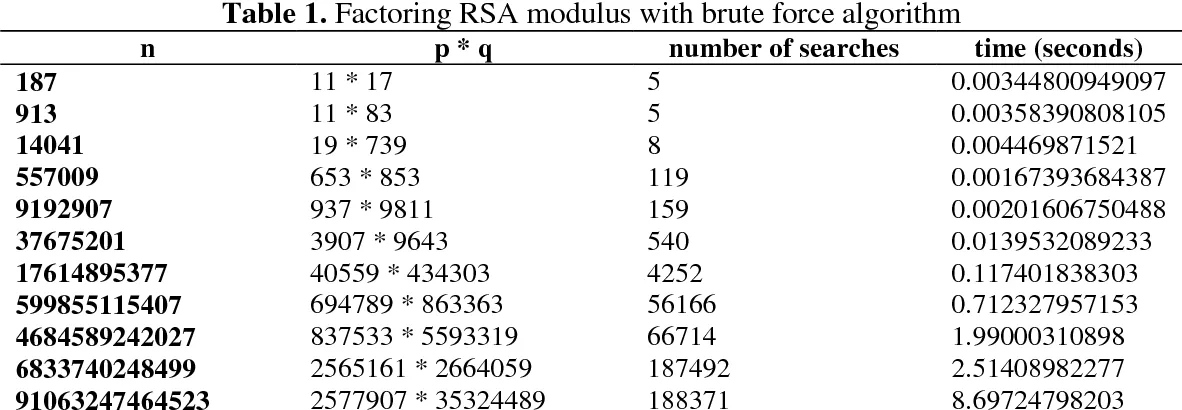
To obtain the recipient’s private key, the modulus , which is available in public needs to be prime factorized. Modulus is obtained by the product of two prime number and , we would need to find these numbers. After that, the and will be used to calculate the Carmichael totient’s function to obtain the private key , which is used to decrypt the message.
The difficulty of breaking RSA comes when factoring large composite numbers into their prime factors. Modulus is obtained by the product of two prime number (product of two prime number is always a composite number), however, factoring large numbers is computationally challenging. As long as the key sizes used in RSA are sufficiently large, it is considered secure against brute force attacks.
The level of RSA security can be chosen by how many bits used for prime numbers and :
- 1024-bit RSA: The modulus is 1024 bits, each prime factor and would be roughly 512 bits.
- 2048-bit RSA: is 2048 bits, and is 1024 bits.
- 3072-bit RSA: is 3072 bits, and is 1536 bits.
- 4096-bit RSA: is 4096 bits, and is 2048 bits.
By having 2048 bits for , it means can vary from to , which is approximately equal to . Consider the table below, the time grows exponentially. For reference, is approximately 47 bits.