Diffie-Hellman
Main Source:
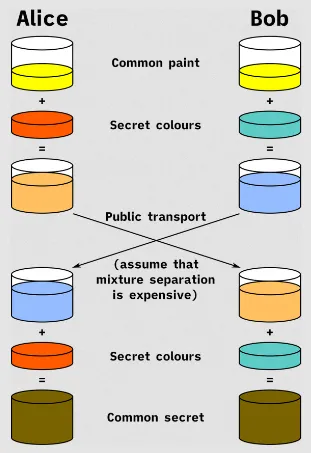
Diffie-Hellman Key Exchange is a cryptographic protocol to securely exchange a secret key over a public communication. It was one of the earliest example of public-key cryptography or asymmetric cryptography.
Explanation
Section titled “Explanation”The Diffie-Hellman key exchange is based on mathematical concepts including the modular exponentiation and the difficulty of the discrete logarithm problem. The protocol relies on mathematical operations performed in a finite field.
- Public Key Agreement: Each party, often denoted as Alice and Bob, agree on two number: , which is a prime number and , which is the base value.
- Key Generation: Both parties choose their own private key (an integer), let’s say Alice’s private key is and Bob’s private key is .
- Public Key Calculation: Alice’s public key (denoted as ) is obtained by , and for Bob (denoted as ) is similar: . After the calculation, they will share the public key to each other.
- Compute Secret Key: The shared secret key, denoted as is computed as follows: For Alice, . Similarly, for Bob, .
That’s it, they will have the same secret key. The secret key is not shared in public, they will derive the secret key on their own. Although they chose a different number (their own private key), they will still arrive at the same secret key.
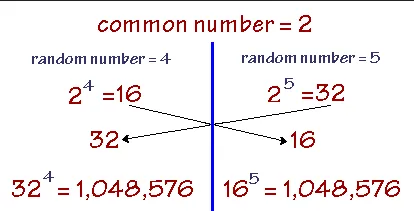
The most important math properties of why this works is described as the following formula:
or
This equation demonstrates that if Party A raises the result of to the power of and takes the modulus , it will yield the same result as Party B raising the result of to the power of and taking the modulus . This property allows both parties to compute the same shared secret key without directly exchanging their private keys.
Source: https://www.pcmag.com/encyclopedia/term/diffie-hellman
Here is an analogy of Diffie-Hellman key exchange in terms color combination.
Security
Section titled “Security”If an attacker were to brute force the secret key, the attacker would need to compute the secret key formula, which is or . Note that only and are kept secret, all the other values such as , , , and are sent in clear.
The hacker would need to solve for , which is equal to the secret key formula. As , , grow larger, the complexity grows exponentially, making it computationally infeasible for large values. Therefore, it is crucial to select larger values to ensure the security of the Diffie-Hellman key exchange.