Mobile Security
Main Source:
- Many Google searches
Mobile is another devices that might be a target for attacks. Phone is something that everyone have, people uses mobile devices for bank transactions or payment, communication, text messaging, etc.
Permissions Exploit
Section titled “Permissions Exploit”In mobile operating system like Android, malicious apps can tricks user into granting excessive permissions to an app, allowing it to access sensitive data or perform unwanted actions. This can happen by tricking user through social engineering.
Clickjacking
Section titled “Clickjacking”Clickjacking is the technique where attacker hide elements on a mobile app’s user interface to deceive users into clicking on unintended buttons or links. This can lead to unintended actions, such as granting permissions, making unwanted purchases, or revealing sensitive information.
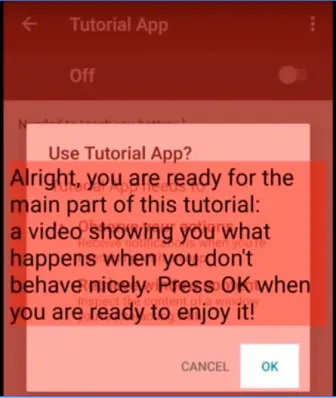
Source: https://9to5google.com/2017/05/26/cloak-dagger-android-vulnerability/
In the image above, the malicious app cover up the system window that ask for permission.
Biometric Spoofing
Section titled “Biometric Spoofing”Biometrics is the measurement of unique physical or behavioral characteristics of individuals. Biometrics are commonly used for identification or authentication, as it is unique to each person, and it will always available. Example of biometrics measurement are fingerprint, facial recognition, iris, retina, voice.
Biometric spoofing is a technique to trick the biometric authentication system by various methods such as using high-resolution photos, artificial fingerprints, 3D models, or identify the weakness of system that recognize them.