DSA
Main Source:
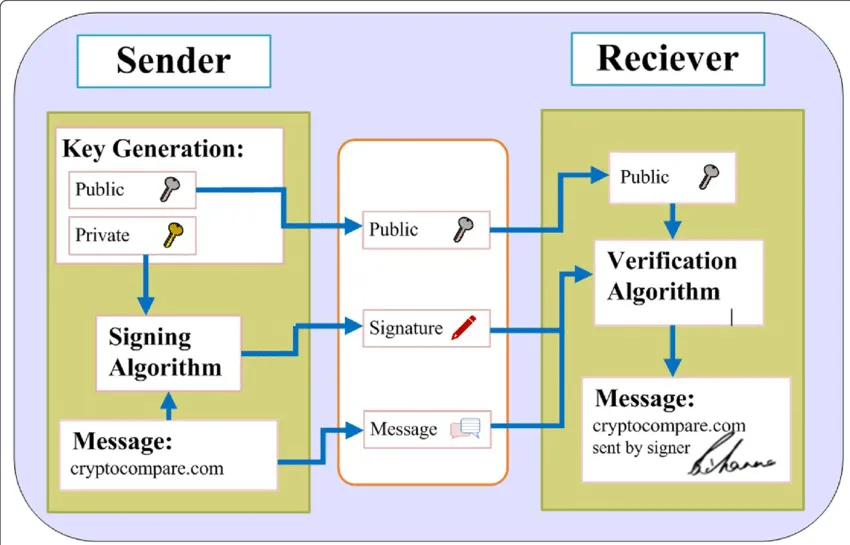
Digital Signature Algorithm (DSA) is a public key cryptography or asymmetric cryptography algorithm used for digital signatures. Digital signature is like a real physical signature, it is used to ensure integrity and origin of digital data.
DSA is based on the mathematical concept of modular exponentiation and the difficulty of solving the discrete logarithm problem. DSA and Diffie-Hellman key exchange both rely on the computational difficulty of the discrete logarithm problem.
Explanation
Section titled “Explanation”The discrete logarithm problem is finding the exponent number in the equation , where is base value, is the result of , and is a prime number. The is the private key which is kept secret, the remaining, , , and are the public keys.
Here is a more detailed explanation of DSA:
-
Key Generation:
-
Choose parameters:
- Choose a hash function with output length of bits (e.g., SHA-1 or SHA-2).
- Choose key length , it should be multiple of 64 between 512 bits and 1024 bits inclusive (or even larger).
- Choose modulus length , should be lower than key length and hash function’s output. For example, and can be (1024, 160), (2048, 224).
- Choose -bit prime and -bit prime , such that is a multiple of
- Choose a random integer from .
- Compute generator : .
- The , , and can be shared publicly.
-
Compute keys:
- Choose random integer as private key from
- Compute public key :
-
-
Key Distribution:
- The (signer) of the digital data should public the public key , whereas the is kept secret.
-
Signing:
- Choose a random integer from .
- Compute .
- Compute , where is the output of hash function when inputting message .
- The resulting signature is the pair , which will be attached to the document.
-
Signature Verification: Given a pair of signature , to determine if it’s valid for message :
- Verify that and .
- Compute .
- Compute .
- Compute .
- Compute .
If is equal to , then the signature is valid.
In conclusion, the public key is used to verify the signature, while the private key (which is hard to find) is used to sign the digital data.
When an attacker tries to break DSA, their objective is to impersonate the original owner. They will try to find the private key so they can modify the content of digitally signed messages without invalidating the signature. This can lead to the manipulation or corruption of data, potentially causing harm or deception.
If we say the document is , the hashed document is , and the hashed document encrypted with private key is , then, the attacker must find the original private key owned by the actual signer, so that the decryption of digital signature or converting back from to will match the hashing of document from to . The verification process doesn’t check if document is modified or not, the point is, the resulting hash value from the document must match with the decrypted digital signatures attached in the document.
Source: https://medium.com/@21_000_000/digital-signature-algorithm-60c8318cf9b6